You’re concerned about keeping your data safe. Data masking is a key method to protect sensitive information. This article breaks down two types, static vs dynamic data masking — what they are, their differences, and their pros and cons.
Keep reading to learn which one, Static vs Dynamic Data Masking, fits your needs best.
Table of Contents

Key Takeaways
- Data masking keeps private information safe by changing real data into something that looks real but isn’t. Static Data Masking (SDM) does this permanently for things like testing, while Dynamic Data Masking (DDM) changes it on-the-go, useful for viewing reports.
- SDM is best for keeping copies of your data secure without affecting the original, making it great for development and cloud transfers. DDM is key when you need to protect info in live settings, like customer support or read-only access, because it masks info right as someone looks at it.
- There are pros and cons to both types. SDM makes sure sensitive details are gone for good which helps with laws and rules about privacy. But, it can’t help with the actual live data. On the other hand, DDM protects live data instantly but might slow things down a bit or be tricky to set up just right.
What Is Static Vs Dynamic Data Masking?
Overview of Data Masking
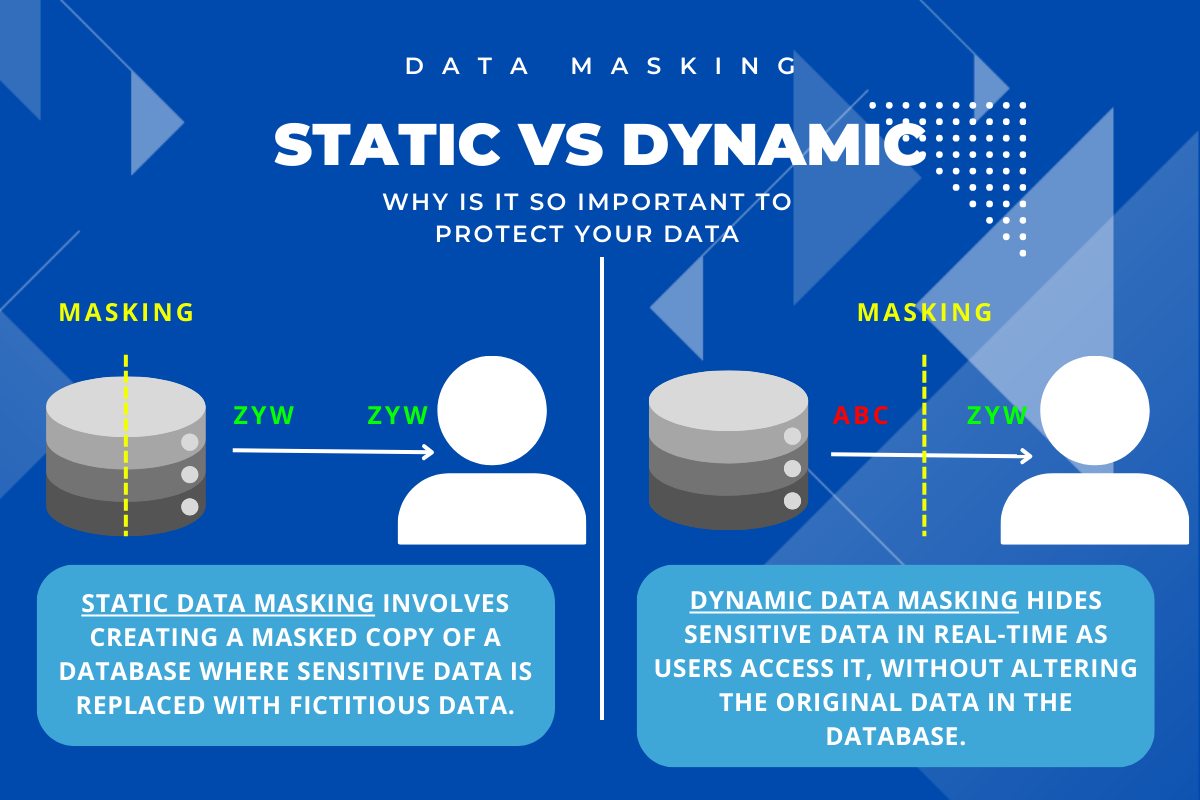
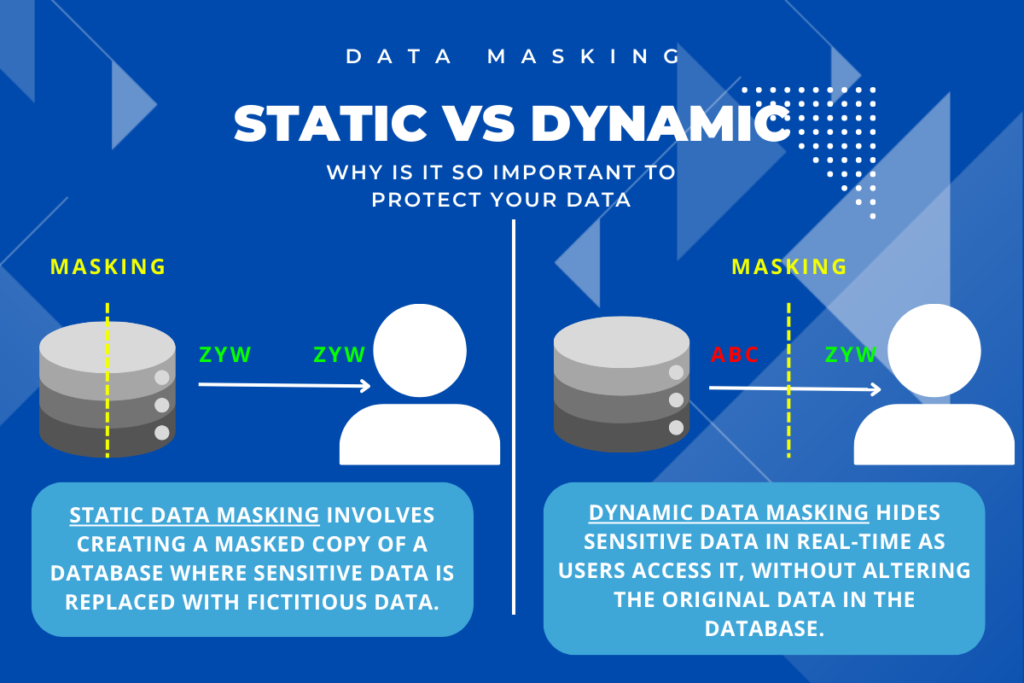
Data masking is crucial to protect sensitive information in databases. There are two primary types: Static Data Masking (SDM) and Dynamic Data Masking (DDM). Each has its own use cases, advantages, and drawbacks.

Static Data Masking (SDM)
Static Data Masking (SDM) changes your sensitive data for good. It takes your real data and turns it into something that looks real but isn’t. This means you can use the changed data safely for things like software tests without risking your private information.
SDM follows strict rules to make sure this new data still works like the original. This is perfect when you need to follow privacy laws or protect your info in the cloud.
SDM doesn’t just swap out a few details; it transforms entire databases in a way that keeps them useful for developers and testers, but safe from prying eyes. You get peace of mind knowing your compliance boxes are ticked off with GDPR, HIPAA, and more.
Plus, financial institutions and healthcare organizations love it because it gives them high-quality test data without exposing personal details.
In the realm of database security, Static Data Masking stands out by turning sensitive information into a fortress—impenetrable yet fully functional for development.
Dynamic Data Masking (DDM)
Dynamic Data Masking (DDM) changes sensitive data as it moves, without altering the original data stored. This technique is perfect for scenarios where you only need to view data, like reports or customer support questions.
DDM uses database and web proxies or built-in features from database vendors to mask data on-the-fly, applying different masks based on user roles. For example, a service agent may see only the last four digits of your credit card during a transaction inquiry.
With DDM, you can choose from full, partial, random or custom masking options to fit various needs in real-time applications and ensure data privacy. It provides strong protection for personal details like email addresses and credit card numbers by showing masked information according to access controls set for different users.
Database systems like SQL Server and tools like APIs play a big role in implementing DDM efficiently in cloud environments or within your network, helping maintain regulatory compliance such as GDPR while minimizing risks related to exposure of personally identifiable information (PII).
Key Differences Between Static vs Dynamic Data Masking

Pros and Cons of Static vs Dynamic Data Masking
Let’s dive into the pros and cons of Static vs Dynamic Data Masking. These insights will help you make informed decisions based on your data security needs.
| Static Data Masking (SDM) | Dynamic Data Masking (DDM) | |
|---|---|---|
| Pros | Permanently removes sensitive data from the data store. No impact on transactions. Protects data copies from various access methods. Simplifies securing data copies. | Enhances security and privacy. Protects data in read-only situations. Works in near real-time. No need for upfront batch processing. |
| Cons | Batch processing if data volume is large. Cannot protect the production database. Permanently changes underlying data. | Not suitable for dynamic environments. Performance overhead. Detailed mapping requirements. Single point of failure. Potential bypassing by users. |
Choosing between SDM and DDM depends on your specific needs. If permanent data alteration is acceptable and the data doesn’t need to be dynamic, SDM might be the right choice. For a more flexible scenario where data needs to remain intact and security must be enforced in real-time, DDM offers compelling benefits despite its complexities.
Static Data Masking (SDM) involves masking data permanently at rest, while Dynamic Data Masking (DDM) masks the data dynamically in real time. SDM is beneficial for non-production environments, while DDM is advantageous for applications where real-time masking is required.
Each approach has its own set of pros and cons that need to be carefully considered during implementation.
Use Cases
Data masking keeps your private information safe. It changes the original data into a version that looks real but isn’t. Here are some ways people use this method:
- Developers make use of static data masking while creating new software. They work with fake yet realistic data, which ensures the original sensitive information stays protected during design and testing phases.
- Companies often transfer data to the cloud safely using static data masking techniques. This is because it removes personal details from the data before moving it, reducing risks.
- In training scenarios, organizations adopt static data masking to protect privacy. Trainees handle masked data similar to actual datasets without accessing sensitive information.
- For live analytics, dynamic data masking proves invaluable. It masks sensitive information in real-time, offering analysts up-to-date but secured data.
- When providing customer support or access to external users, businesses apply dynamic data masking solutions. This approach allows users to query databases without exposing confidential details.
- Protecting read-only transactions becomes essential in sectors like banking or healthcare; here, dynamic data masking offers a layer of security by instantly obscuring specific data elements in transaction records viewed by unauthorized personnel.
- Compliance with laws such as the General Data Protection Regulation (GDPR) is another critical use case for both types of masking techniques—ensuring personal information is obfuscated or anonymized to meet legal standards.
- Research teams benefit from dynamic data masking when conducting statistical analysis or accessing medical records for studies without compromising patient confidentiality.

These strategies not only help protect sensitive information but also allow organizations to maintain the utility of their datasets for development, analysis, and compliance purposes—ensuring privacy and enhancing security measures across various operations.
Conclusion – Static vs Dynamic Data Masking
In conclusion, data masking is a crucial practice for organizations handling sensitive data. Understanding the differences between static and dynamic data masking is essential for making informed decisions about securing your data.
Both static and dynamic data masking have their distinct advantages and use cases that cater to different needs of an organization. By employing the right type of data masking, you can ensure the protection of sensitive information while enabling secure development and testing processes.
With this knowledge, you are well-equipped to make strategic choices in safeguarding your valuable data assets.
FAQs about Static vs Dynamic Data Masking
1. What’s the difference between static vs dynamic data masking?
Static data masking changes your original data into a new, permanent form. It’s great for testing or training when you don’t need real-time data. Dynamic data masking, on the other hand, masks sensitive information in real-time without altering the original data. This means when you access databases like Microsoft SQL Server or PostgreSQL, it shows masked data based on your role.
2. When should you use static masking?
Use static masking for tasks where you need to protect sensitive information but still work with realistic-looking data, such as software testing or statistical analysis. It keeps your encrypted info safe even when using spreadsheets or sharing files.
3. Why choose dynamic over static?
Dynamic masking shines in live environments where users interact with current health insurance portability and accountability act (HIPAA) compliant health information or financial records. It allows immediate access while hiding personal details through methods like randomization or shuffling – all without changing the actual stored records.
4. Can both types of masking secure big data?
Yes! Both strategies can handle large volumes of info across platforms like Amazon Web Services (AWS). Static helps create synthetic datasets for deep analysis without exposing real stats, while dynamic ensures only authorized eyes see sensitive bits during live queries.
5. What tools help with these types of maskings?
For static, look towards software that specializes in persistent encryption and tokenization to transform and fix your dataset securely; think anonymization tools tailored for regression testing scenarios where accuracy is key but so is privacy.
Dynamic relies more on proxy servers that sit between users and databases – applying rules-based masks depending on who’s asking what – ensuring compliance with regulations by protecting strings of personal identifiable information (PII) dynamically.
6. Are there any cons to using these methods?
The main challenge lies in balancing security with usability; too much obfuscation may hinder user experience or complicate legitimate research efforts requiring precise correlations among datasets.
Additionally, implementing robust cryptographic algorithms requires expertise not just at setup but throughout its lifecycle to adapt defenses against evolving threats while maintaining system performance.