You’re facing a challenge: protecting sensitive information in an online world.
Data masking vs data encryption are two powerful tools in this fight. This article explains the differences between data masking vs encryption, guiding you on when to use each method effectively.
Stay safe out there with data masking vs encryption!
Table of Contents
Key Takeaways – Differences between Data Masking Vs encryption
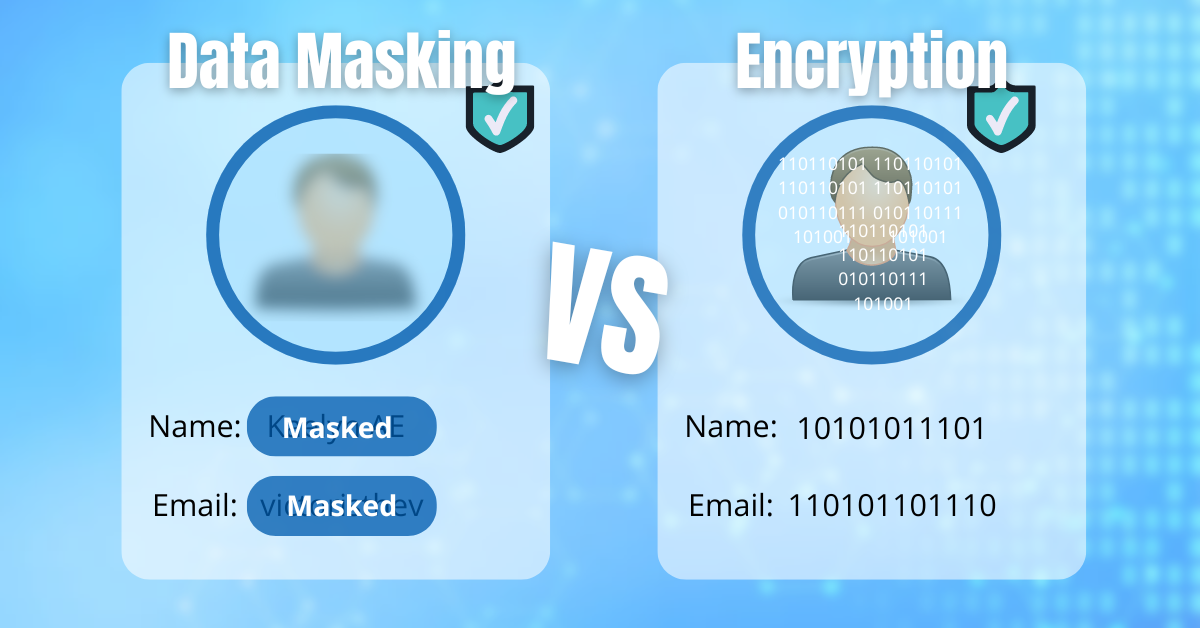
- Data masking changes sensitive information so it looks real but isn’t, and you can’t change it back. It’s used to keep data safe while meeting rules like PCI DSS for payment cards or HIPAA for health info.
- Data encryption turns sensitive data into a secret code that only people with a key can read. It’s like sending a locked box that only the receiver can open, keeping communication and stored data secure.
- While data masking is great for creating safe copies of real data for testing or development without risking privacy, encryption is best for protecting data being sent over networks or kept for a long time.
- Data masking makes sure even if someone sees the masked version of your information, they won’t learn anything useful about you. It’s ideal when sharing datasets for analysis without exposing private details.
- Encryption is essential in online banking and secure messaging systems where sensitive info must be protected during transfer or long-term storage to prevent unauthorized access.
What is Data Masking?
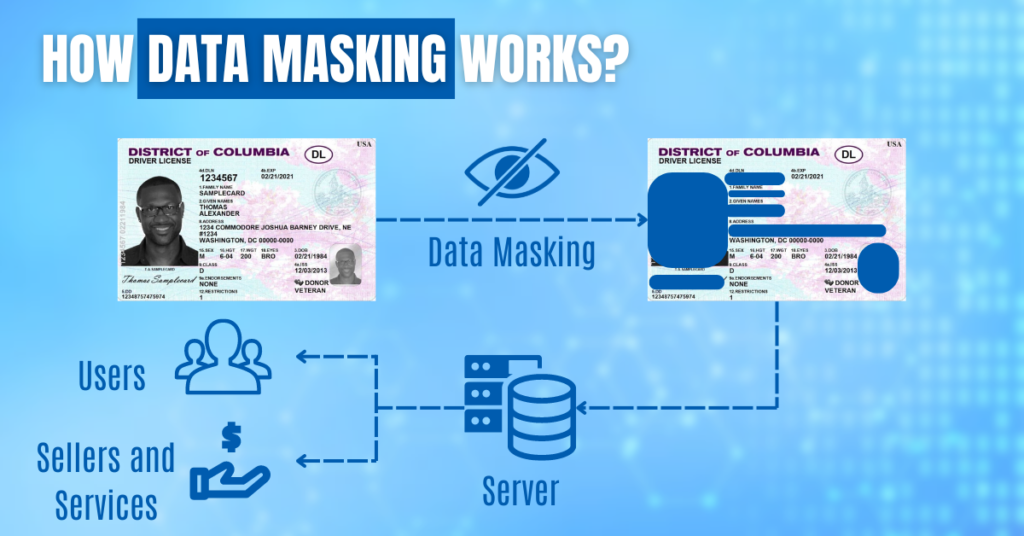
Moving from the basics, let’s talk about data masking. Data masking changes sensitive information so it looks real but isn’t. Think credit card numbers or social security numbers; this method swaps them with fake data that doesn’t link back to any real person.
It is a sure way to keep structured data safe. You see these methods in action when companies need to meet rules like PCI DSS for payment cards or HIPAA for health info.
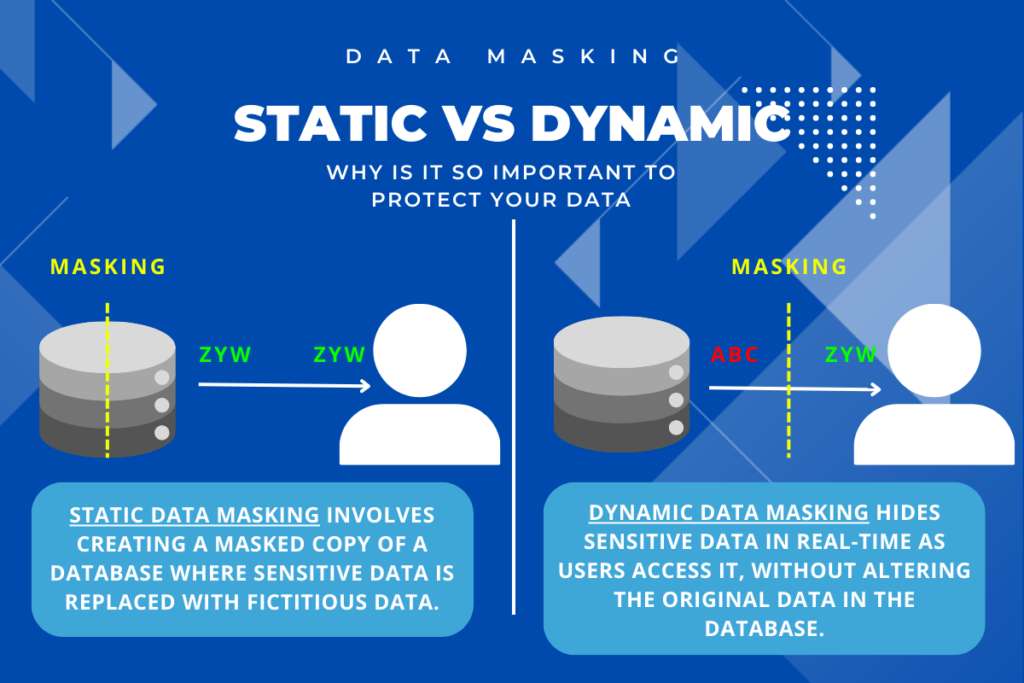
For example, if someone tried to peek at masked data, all they would see are values that seem legit but lead nowhere—like looking at a map with made-up street names. Types of data masking such as static, dynamic, and on-the-fly handling mean businesses can pick how they secure their data based on what they need.
Static keeps the original safe by making a duplicate with the fake values for testing or development without risking the real info.
Data Masking: Turning sensitive details into bold fakes keeping hackers clueless and compliance checkers happy.
What is Data Encryption?
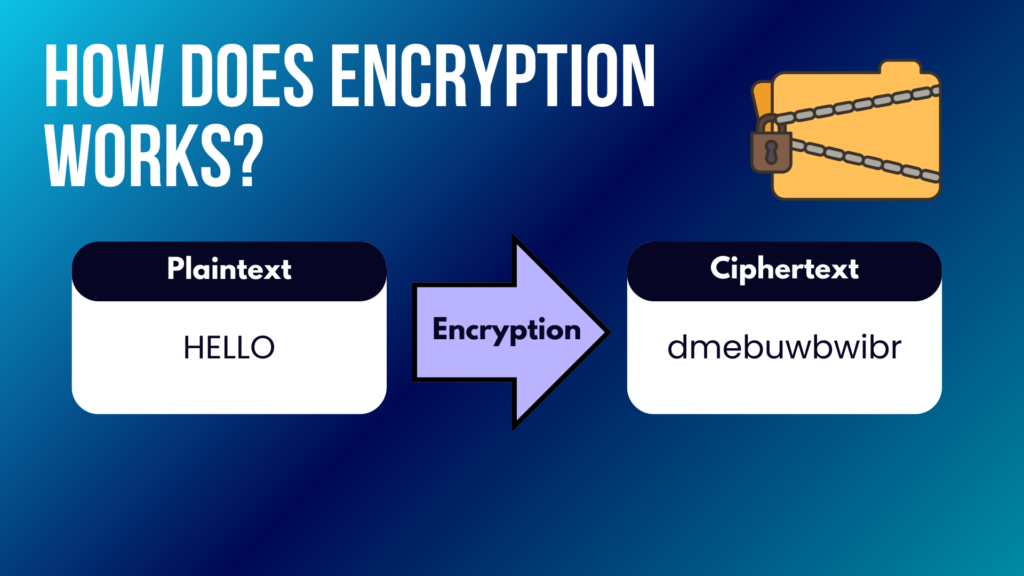
Data encryption changes sensitive data into a secret code. Think of it as turning your messages into a puzzle only certain people can solve. This process uses complex math called algorithms, like AES256 and RSA.
To read the encrypted message, you need a special key. Without this key, the information looks like random letters and numbers.
Imagine sending a locked box through the mail. If you have the key, you can open it easily once it arrives. Data encryption works similarly for digital information—keeping files, videos, and images safe while they move across networks or sit in storage.
Only with the correct decryption key can someone unlock and read the data inside. This way, your personal details stay protected from anyone who shouldn’t see them.
Comparing Data Masking vs Encryption
Data masking makes data look real but it’s irreversible. Encryption changes the data, and you can change it back. Data masking lets you use the info normally after changing it. Encryption changes the way you can use the data.
Want to learn more about the important differences between data masking vs encryption? Read on!
Irreversibility of Data Masking
Once data masking changes your information, you can’t change it back.
This is why it is better to have a backup before masking your data.
This method keeps your data safe by replacing sensitive details with similar, but not real, values. For instance, if your original data is a social security number, data masking might change it to look like a random set of numbers that has nothing to do with the actual number.
This way, even if someone gets hold of the masked data, they won’t learn anything useful about you.
Data masking tools ensure your privacy in various situations – whether it’s keeping customer info safe in databases or making sure employee records stay confidential. To put this into perspective: Imagine sending a letter without including your home address on the envelope.
Even if the wrong person opens it, they won’t know where you live because that vital piece of information is missing. That’s how effective and irreversible data masking works; once applied, there’s no going back.
With Data Masking, what’s done is done – ensuring absolute security for your sensitive info.

Data Usability Post-Processing
After data masking, the usability of the data is limited because it’s meant to secure sensitive information like credit card numbers and personal details. The post-processing of this masked data aims to restore its functionality for authorized users while still keeping the sensitive information protected.
This process ensures that while using the data for analysis or testing, only relevant and necessary details are visible, preserving the confidentiality and integrity of the original sensitive information.
It provides a balance between security and usability by allowing functional access without exposing critical details.
Security Levels
Data Masking vs Encryption both offer different security levels for your sensitive information. Data Masking obscures the actual data, making it unusable to unauthorized users. It allows specific people or systems to see only part of the data, while others can’t access it at all.
On the other hand, encryption converts the original data into a secret code that can be decoded only with a special key. It can use symmetric or asymmetric data encryption methods.
When considering security levels, it’s important to choose the right method based on your specific data needs and regulations. For instance, if you need to comply with strict privacy laws such as GDPR or HIPAA, you may opt for data masking which desensitizes all identifiable information completely.
In contrast, encryption ensures that even if someone gains access to the encrypted data, they won’t be able to understand or use it without permission.

Applications of Data Masking and Encryption
Data masking is widely used in situations requiring realistic test data for software development or testing. For instance, it’s essential when dealing with sensitive information like personal identification numbers and credit card details.
Encryption finds its application in securing communication channels, especially in areas such as online banking and secure messaging systems.
Situations for Data Masking
In some cases, data masking is crucial to protect sensitive information. Here are scenarios where data masking is essential:
- Testing Environments: When you need real production data for testing software or applications.
- Compliance Requirements: Ensuring that your company complies with privacy regulations like GDPR and HIPAA.
- Outsourcing Development: Sharing data with external developers while protecting sensitive details.
- Data Analytics: Sharing datasets for statistical analysis without exposing private information.
- Cloud Migration: Moving data to the cloud securely, especially when working with third-party vendors.
Situations for Encryption
When it’s necessary to protect data that’s being transferred between computers or networks, or stored for a long time, encryption is the way to go. Here are some specific situations where encryption is used:
- Secure Data Transmission: When sensitive data needs to be sent from one place to another, such as credit card information during an online purchase.
- Long-Term Data Storage: If you need to store sensitive information for a prolonged period, like personal records in a database.
- Protection of Information at Rest: When safeguarding data that’s stationary, like the contents of a hard drive or database on a server.
- Compliance with Regulations: Meeting the requirements of industry standards and government regulations, like the Health Insurance Portability and Accountability Act (HIPAA) or General Data Protection Regulation (GDPR).
- Sensitive Information Exchange: Use encryption when exchanging key data, such as bank transactions or healthcare records among different systems or organizations.
Conclusion – What is data masking vs encryption?
In the end, you’ve learned that data masking vs encryption have key differences in protecting your sensitive information. Data masking replaces sensitive values with algorithmically determined ones for compliance purposes while still being functional.

On the other hand, data encryption scrambles data to make it unreadable until decrypted with a specific key. Both are crucial for safeguarding different types of data and ensuring compliance standards like GDPR and HIPAA are upheld.
Keep these distinctions in mind when securing your valuable information.
FAQs – Data Masking Vs Encryption
1. What’s the difference between data masking vs encryption?
Data masking and encryption are two different data security techniques. Data masking involves changing or hiding original data, like personally identifiable information, with obfuscation methods such as pseudonymization or tokenization. On the other hand, encryption converts plaintext into ciphertext using an encryption key in a process that can be reversed (decrypted) using a decryption algorithm.
2. How does data compliance come into play with these techniques?
Both techniques help achieve GDPR and HIPAA compliance by protecting sensitive information like protected health information (PHI). They prevent unauthorized access thus reducing the risk of breaches which is crucial for meeting data privacy laws requirements.
3. Can you explain symmetric and asymmetric encryption?
Sure! Symmetric encryption uses one secret key to both encrypt and decrypt the data while asymmetric encryption uses two keys – a public key for encrypting and a private key for decrypting.
4. Is there any specific situation where I should use one technique over another?
If your concern is maintaining integrity while testing software, you might prefer dynamic data masking to keep actual values hidden yet functional… If it’s about securing stored ‘data at rest’ or transmitting ‘data in use’, then consider AES-256 or RSA Encryption based on needs…
5. Are both techniques equally secure against cyber threats?
While both provide robust cybersecurity measures… they have their vulnerabilities too… For instance, encrypted text could potentially be brute-forced decrypted given enough time… Masked info can’t be reverse-engineered without knowledge of exact method used…
6. Does choosing between them affect my business operations significantly?
Not necessarily… With right implementation, neither should disrupt normal operations… But do remember – proper management of decryption or de-identification processes is vital to ensure smooth functioning…